CrowdStrike has released its 2025 Global Threat Report, exposing the growing aggression of China’s cyber operations, a surge in gen AI-powered social engineering and nation-state vulnerability research and exploitation, and a sharp increase in malware-free, identity-based attacks.
Tracking more than 250 named adversaries and 140 emerging activity clusters, CrowdStrike’s latest research reveals that China-nexus adversaries escalated state-sponsored cyber operations by 150%, with targeted attacks in financial services, media, manufacturing and industrial sectors soaring up to 300%.
At the same time, adversaries worldwide are weaponising AI-generated deception, exploiting stolen credentials and increasingly executing cross-domain attacks—exploiting gaps across endpoint, cloud and identity—to bypass security controls and operate undetected in the shadows. The shift to malware-free intrusions that exploit trusted access, combined with record-shattering breakout times, leaves defenders little room for error, CrowdStrike said.
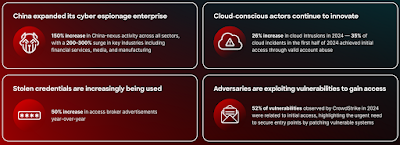 |
| Source: CrowdStrike infographic. China is increasingly active in cyber espionage. |
Report highlights include:
China’s cyber espionage grows more aggressive
CrowdStrike identified seven new China-nexus adversaries in 2024, fuelling a 150% surge in espionage attacks. Critical industries saw up to a 300% spike in targeted attacks.
Gen AI supercharges social engineering
AI-driven phishing and impersonation tactics fuelled a 442% increase in voice phishing (vishing) between H124 and H224. Groups like CURLY SPIDER, CHATTY SPIDER and PLUMP SPIDER leveraged social engineering to steal credentials, establish remote sessions and evade detection.
Iran uses gen AI for vulnerability research and exploitation
In 2024, Iran-nexus actors increasingly explored gen AI for vulnerability research, exploit development and patching domestic networks, aligning with government-led AI initiatives.
Surge in malware-free attacks
Seventy-nine percent of attacks to gain initial access are now malware-free while access broker advertisements surged 50% year-on-year. Instead of using malware, adversaries exploited compromised credentials to infiltrate systems as legitimate users, moving undetected laterally.
Insider threats continue to rise
DPRK-nexus adversary FAMOUS CHOLLIMA was behind 304 incidents uncovered in 2024. Four in 10 involved insider threat operations, with adversaries operating under the guise of legitimate employment to gain system access and carry out malicious activity.
Breakout times hit record speeds
The average e-crime breakout time dropped to 48 minutes, with the fastest recorded at 51 seconds—leaving defenders little time to react.
Cloud environments under siege
New and unattributed cloud intrusions increased by 26% year-on-year. Valid account abuse is the primary initial access tactic, accounting for 35% of cloud incidents in 1H24.
Unpatched vulnerabilities a key target
Over half (52%) of vulnerabilities observed were related to initial access, reinforcing the critical need to secure entry points before adversaries establish persistence.
“China’s increasingly aggressive cyber espionage, combined with the rapid weaponisation of AI-powered deception, is forcing organisations to rethink their approach to security,” said Adam Meyers, Head of counter adversary operations at CrowdStrike.
“Adversaries exploit identity gaps, leverage social engineering and move across domains undetected—rendering legacy defenses ineffective. Stopping breaches requires a unified platform powered by real-time intelligence and threat hunting, correlating identity, cloud and endpoint activity to eliminate the blind spots where adversaries hide.”
Explore
Download the 2025 CrowdStrike Global Threat Report at https://www.crowdstrike.com/en-us/global-threat-report/
No comments:
Post a Comment